IOT is even more of a risk than you thought
GRIMM purchased a GeoVision camera that arrived off-the-shelf with security vulnerabilities like most consumer IOT devices. The camera is a stand-in for any IOT device in a residential, industrial, or enterprise environment. The team demonstrated through a practical hands-on-exercise at HackNYC, RSA, Hack the Capitol, and multiple BSides where participants learn how to use a publically available exploit to compromise an emulated home network.
The team modeled the design and configuration of the hands-on-exercise from a traditional use case:
- A router with a forwarded network port
- A publicly accessible IOT camera
- A Windows computer that stored a treasure trove of valued, personal data
Though the traditional use case may well be known as a textbook style situation, newer products offered by IOT vendors such as Nest and Ring leverage cloud-based services to simplify the technical burdens that an end-user may endure when configuring an IOT device. For the majority of IOT consumers, the cost of the device puts significant weight into the consideration of whether to go with a more name-branded solution or a significantly cheaper alternative.
The tradeoff that motivates many consumers when selecting an IOT device summarizes into three key points:
- Cost: There are hundreds upon thousands of IoT devices filling the markets ranging from refrigerators, sprinkler systems, pet feeders, to even a smart egg tray. One of the more significant choices to consumers’ views is whether they are willing to spend the bare minimum price for a particular product or fork over the high dollar amounts for the named-branded systems. Another factor in addressing cost revolves around the concept of features, technologies, and vendor-specific solutions.
- Meeting the Objective: Whether it’s to satisfy a goal such as home security or the choice of splurging on money due to a whim–consumers set the goals and decides how its met.
- Ease-of-use and support: Many households and families often have a mixture of techno-savvy users to technical-incompetent individuals. Of which, a majority of these characteristics arise during the holidays when the technical folks are faced with a daunting list of IT help desk style issues by their family members during the holidays. For an IOT device, the audience of the product has a significant factor in the decision process in terms of technical skill sets. Does a technical-incompetent grandmother want to be faced with even the slightest thought on how to forward a network port on a router or even attempt to update Windows on their smart fridge? The most likely answer would probably be “no,” but there are of course outliers to every situation. Weighing the audience in the decision-making process, many of the more expensive products like Ring and Nest offer the simple solution where their devices automatically receive updates through their respective cloud service, the technical-incompetent user can naturally interact with their IoT device using a smartphone, and have met their overall objective.
The GeoVision camera met all the objectives a home user would consider when choosing a system for home surveillance and security. The initial cost of the camera at the time of purchase varied between $49.00 to $79.99 of which, if a consumer needed multiple cameras to cover the various angles of their home, the price per unit was affordable when compared to that of Ring or Nest. Cost-wise, the GeoVision camera was one of the cheapest devices in the market to provide surveillance, but when considering ease-of-use, many issues arose including the potential burdens of setting up the camera.
The not so Simple Camera Installation
Setting up the GeoVision camera wasn’t a straightforward process as the accompanied quick start guide was a whopping 331 pages of documentation with example figures using a Windows XP machine. Physically, there’s minimal effort needed to install the camera as it only required an active ethernet cable and a power adapter. Alternatively, consumers may use a Power over Ethernet (PoE) if available. The software configuration of the camera required an individual with a level of technical skills that has knowledge of locating the IP address of a camera and configuring a home router.
Accessing the web interface of the GeoVision camera, and authenticating using a generic password, the user would finally be able to view the camera’s live feed as shown in Figure 1.
Figure 1. The GeoVision web interface for the camera
After setting up the camera and getting the appropriate configuration needed to allow users to access the system from the Internet, maintaining the camera’s updates require another level of effort of which–would most likely be overlooked by the end-user as the camera does not provide any indication of a new patch release or an automated way to update the system.
A Risk Ready to Happen
There are two different ways in which a consumer may access an IOT device. The first approach involves selecting a vendor that uses their cloud services to connect the consumers’ devices to the vendor’s network. The second approach involves the traditional use case we have mentioned where the consumer forwards a port on their router and publicly exposes the IOT device for public access on the Internet. The security controls behind the latter involves a combination of a username and password, but if the device itself has a security vulnerability and an attacker has code to exploit the system, then a username and password would be useless as the attacker could easily bypass the login prompt. Figure 2 depicts a common Internet crawler resource an attacker may use to identify devices on the Internet. For the example case, we searched for systems that was running a web service with the phrase GeoVision.
Figure 2. Censys provides a listing of GeoVision cameras
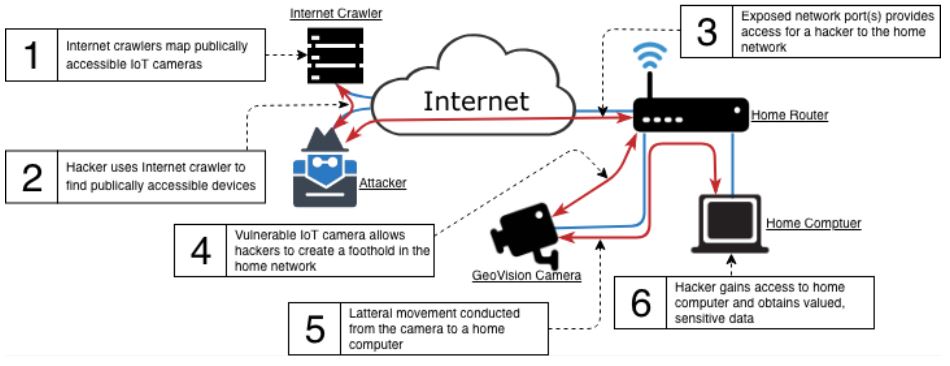
As we see from the diagram, there are 1,679 potential devices on the Internet at the time of search that uses the phrase GeoVision. For an attacker’s perspective, they would write a script to automatically attack all devices listed in the search result from the Internet crawler. Figure 3 depicts the attacker’s journey from identifying an IOT device using an Internet crawler to compromising a consumer(s) home network by means of leveraging an exploit.
Figure 3. The attacker’s journey
An Exercise for the Reader
This post has listed many key points and topics of the IOT realm and we wouldn’t want you to simply start downloading every exploit publically accessible and launching the code widely on the Internet. Therefore, we provide a home lab exercise for you to practice your hands-on skills. Although there are some limitations with the exercise such as obtaining an IOT camera, the practical exercise walks you through the attacker’s journey.